The Complete Hacking Course Beginners to advanced free
"World War III is going to be a cyberwar"
~BLOG CONTENTS.
Things you will get to know after reading this Blog.
1.Introduction
2. Is this information enough to learn to hack?
3. Why should we learn to hack?
4. What is hacking?
5.Types of hacking.
6.Advantages and Disadvantages of hacking.
7. Which language is best for hacking?
8. From where I can learn Python for free?
9. Types of hackers.
10. Is hacking worth?
11. Is there any future for hacking?
12 Demands of hackers in the future
13. Syllabus for hacking.
14. Best institution for hacking in India.
15. Tools/Environment Setup required for hacking.
16 Top 10 Hacking courses absolutely free.
17. Top 10 best hacking Websites.
18. Successful Hackers.
19. Indian hackers.
20. My motivation
21. Conclusion
~INTRODUCTION TO HACKING
“It is not the monsters we should be afraid of; it is the people that don’t recognize the same monsters inside of themselves.”
― Shannon L. Alder
So, hello guys if you want to be an ethical hacker and don't know where to start and what to do then fortunately and luckily you came at the correct place. So without wasting any time let's get started.
Hello guys in this blog you will get to know everything from scratch to advanced level about Ethical hacking. The ethical Hacking blog is developed for beginners and professionals. This blog covers all the aspects associated with hacking.
Hacking has been a part of computing for almost five decades and it is a very broad discipline, which covers a wide range of topics.
The first known event of hacking had taken place in 1960 at MIT and at the same time, the term "Hacker" was originated. In this blog, we will take you through the various concepts of Ethical Hacking and explain how you can use them in a real-time environment.
~IS THIS INFORMATION ENOUGH TO LEARN HACKING/HOW TO LEARN HACKING?
Yes, the information which I will be provided in this blog is more than enough to become an ethical hacker. This blog has been made for professionals aspiring to learn Ethical Hacking and make a career as an Ethical Hacker.
So, there is no need to rush another website we will be providing all the essential information and links in this blog.
You can also make some notes from this Blog for future needs.
~WHY SHOULD WE LEARN HACKING?
Bro as I suggested World War 3 is going to be a cyberwar. The world is going at a pace towards HACKING and CYBERSECURITY.
The increasing amount of Internet users also brings responsibility to the servers to have their own hackers and Cybersecurity experts. Otherwise, the security of the users will be of big questions.
The certification of the above may be very helpful.
For Example, if you are using GOOGLE and reading this blog which I have written then you are safe because google hires their own Ethical Hackers as other web servers but if google stops hiring hackers then Black hat hackers(Explained below) can just get your google login information and can get access to your personal information and can use them illegally. So to avoid this Google hires its own hackers to avoid such kinds of online illegality.
~WHAT IS HACKING?
Hacking may be defined as gaining access to a system that you are not supposed to have access is considered as hacking.
Example login into an email account that is not supposed to have access, gaining access to a remote computer that you are not supposed to have access, reading the information that you are not supposed to able to read is considered as hacking. There are a large number of ways to hack a system.
~TYPES OF HACKING.
We can define hacking into different categories based on what is being hacked,
1.Website Hacking.
2.Network Hacking.
3.Computer Hacking.
4.Password Hacking.
5.Email Hacking.
1.Website Hacking: Website hacking means taking unauthorized access over a web server, database and make a change in the information.
2.Network Hacking: Network hacking means gathering information about a network with intent to harm it or damage it.
3.Computer Hacking: Computer hacking means unauthorized access to the computer and steals all the necessary information like PC ID passwords etc.
4.Password Hacking: Password hacking is the process of recovering a password from your computer which has been saved.
5.Email Hacking: It means unauthorized access to emails without the owner's permission.
~ADVANTAGE AND DISADVANTAGE OF HACKING.
Advantages of hacking.
Hacking is quite useful in the following scenarios −
- 1. To recover the lost information like a password.
- 2. To perform penetration testing to strengthen computer and network security.
- 3. To put adequate preventative measures in place to prevent security breaches.
- 4. To have a computer system that prevents malicious hackers from gaining access.
Disadvantages of Hacking
Hacking is quite dangerous if it is done with harmful intent. It can cause −
- 1.Massive security breach.
- 2.Unauthorized system access on private information.
- 3.Privacy violation.
- 4.Hampering system operation.
- 5.Denial of service attacks.
- 6.Malicious attack on the system.
“My actions constituted pure hacking that resulted in relatively trivial expenses for the companies involved, despite
the government’s false claims – Harry Hariom Choudhary.”
― Harry Hariom Choudhary
The answer is Yes.
Hacking needs coding.
PYTHON is the language you need to know which is not so tough and an average person can learn it within 3 months.
You can download it by clicking the link provided below
Download the latest version of python.
~FROM WHERE I CAN LEARN PYTHON FOR FREE?
You can learn python from various websites like
1.YouTube.
2.Udemy.
3.Cybrary.
and many others.
but the best teacher from where I learned to hack is from Telesku.
Click below to get the full python course from scratch to advance level.
Learn Python for free
~TYPES OF HACKERS.
Hackers can be categorized in three different ways.
1.Black Hat Hackers.
2.White Hat Hackers.
3.Grey Hat Hackers.
Black Hat Hacker.
Black-hat hackers are also known as an Unethical Hacker or a Security Cracker.
These people hack the system illegally to steal money or to achieve their own illegal goals. They find banks or other companies with weak security and steal money or credit card information. They can also modify or destroy the data as well. Black hat hacking is illegal.
White Hat Hacker.
White hat hackers are also known as Ethical Hackers or Penetration Tester. White hat hackers are the good guys of the hacker world.
These people use the same technique used by black hat hackers. They also hack the system, but they can only hack the system that they have permission to hack to test the security of the system. They focus on security and protecting the IT system. White hat hacking is legal.
Gray Hat Hacker.
Gray hat Hackers are Hybrid between Black hat Hackers and White hat hackers. They can hack any system even if they don't have permission to test the security of the system but they will never steal money or damage the system.
In most cases, they tell the administrator of that system. But they are also illegal because they test the security of the system that they do not have permission to test. Grey hat hacking is sometimes acted legally and sometimes not.
Comment below which type of hacker you want to be in your life and also if you need to know any information relating it.
~IS HACKING WORTH?
The simple answer to this question is YES.
In the world of digitalization, where the internet has brought the people across the globe closer, it has also caused many issues in terms of online crime and theft. Multiple options and tools are coming up that disrupt the privacy of the person. If you have noticed, Security has become a trending topic among the IT’ians. Even the major companies have faced a lot of financial trouble and breaches because of security issues. The best way to deal with it is to understand how it works and actually works accordingly to that mind map itself. This type of hacking we can call as ethical hacking. Mind you, it is completely legal and currently has got a great scope in the town.
- It is the hacker who makes the sure malicious attack from unknown source gets protected.
- Such a person is capable to use preventive measures to avoid any kind of security breaches
- To make sure the customer or user information is well protected, the hacker comes up with a new solution
- It is the hacker who ensures that the network is tested on the regular note
There is no doubt that if you want to become a hacker, you will be loaded with ample of responsibilities. Ethical hacking is one such field that has got a reputation and a great scope in terms of career. No doubt that money can never be a problem when it comes to paying. But if you are little dicey about ethical hacking, then certainly here are some of the reasons that you need to know.
Now that you are on this page, it is quite obvious that you either must have searched on the right way to become a hacker or why you need to learn to hack. Frankly, it is fun but only till you follow the ethics and don’t misuse the information in any other way. Remember, if you do it for fun, you will be surrounded by special life but with criminal intention, you will have to spend your life in jail.
It is the hacker who builds the computer system in such a way that would protect the access of the hacker and would ensure that the safeguard system are well used
Reasons Need to Learn Hacking
- Good scope for a career.
- Google trend for ethical hacking.
- Worth investing time and money.
- good pay
- Explore in a better way
- No limitations.
CLICK HERE TO KNOW ITS VALUE :)
Hey, now lets me show you some of the images.
So you can see the demand for Ethical hacking in today's world.
It is considered to be the most important skill in the 21st century.
With more and more companies entering the e-commerce ecosystem and adopting new technologies like cloud computing, the threat from imminent security breaches is clearly demanding the need for efficient information security systems. The rising threat from cyber-attacks has exposed a severe shortage of talent in this sector.
As per 2015 figures reported by Nasscom, India needed more than 77,000 white hat hackers as against only a mere 15,000 certified professional ethical hackers in that year.
~DEMAND OF HACKERS IN FUTURE.
In today's digital era, one of the biggest threats comes from cybercriminals. Hackers were not taken seriously until a few years back. Recently, some big names in the Indian industry had to pay hefty sums of money to hackers to keep confidential information from being disclosed to the government. According to surveys conducted by cybersecurity firms in the country, Indian firms lost more than $4 billion in 2013 alone because of hackers.
With more and more companies entering the e-commerce ecosystem and adopting new technologies like cloud computing, the threat from imminent security breaches is clearly demanding the need for efficient information security systems. The rising threat from cyber-attacks has exposed a severe shortage of talent in this sector.
As per 2015 figures reported by Nasscom, India needed more than 77,000 white hat hackers as against only a mere 15,000 certified professional ethical hackers in that year.
~ETHICAL HACKING SYLLABUS PDF.
Following needed to learn.
Network Penetration
- Network Penetration Testing
- Basic of Network
Pre-connection Attacks
- Pre-connection Attacks
- Wireless Interface in Monitor mode
- About airodump-ng
- Run airodump-ng
- Deauthenticate
Gaining Access
- Introduction
- Gaining Access
- WEP Introduction
- WEP Cracking
- Fake Authentication Attack
- ARP Request Replay Attack
- WPA Theory
- Handshake Theory
- Capturing Handshakes
- Creating Wordlist
- Cracking Wordlist
- Securing Network from Attacks
Post Attacks
- Post-Connection Attacks
- netdiscover
- Zenmap
MITM Attacks
- MITM Attacks
- ARP spoofing using arpspoof
- ARP spoofing using MITMf
- Bypassing HTTPS
- DNS Spoofing
Server Attacks
- Server-side Attacks
- Server-side Attack Basics
- Attacks - Metasploit basics
- Exploiting a Code Execution Vulnerability
- Installing MSFC
- MSFC Scan
- MSFC Analysis
- Installing Nexpose
- Nexpose Scanning
~BEST INSTITUTION OF HACKING
To know the best institute for Ethical hacking in India you can click on the link given below.
ClICK ME :)
~SOFTWARE/TOOLS REQUIRED/ENVIRONMENTAL SETUP.
In step1, we download the Virtual box because the virtual box allows us to create a virtual machine inside our current operating system. After this, we will download the Kali Linux. A virtual machine is just like a completely separate working machine. You will lose nothing if you install an operating system inside the virtual machine. The operating system will perform just like the install on a separate laptop.
Now using the following link, you can download the virtual box according to your operating system and install it.
Download Virtual Box
After installation, the virtual box will be shown as follows:
Step 2: Download Kali Linux
Now we will download the Kali Linux. It contained all the programs and application that we need to use pre-installed and preconfigured that means we just need to install this operating system and start hacking.
There are two ways to install Kali. You can install it as a virtual machine inside your current operating system, or you can download it as a main operating system. In this tutorial, I am going to use a virtual machine.
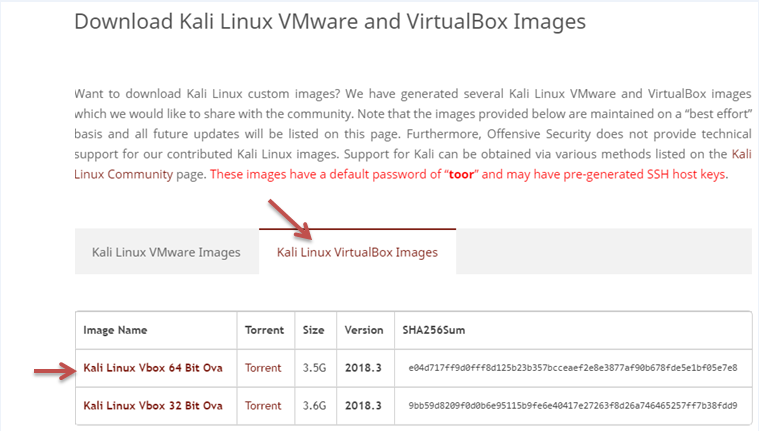
Use the following link to download the Kali Linux operating system.
Now click on Kali Linux VirtualBox Images and download the Kali Linux according to the compatibility of your operating system.
- Download the 64-bit version if your computer is 64 bits otherwise, download the 32-bit version.
- The downloaded file has a .ova extension. If the file doesn't have .ova extension that means you downloaded the wrong file.
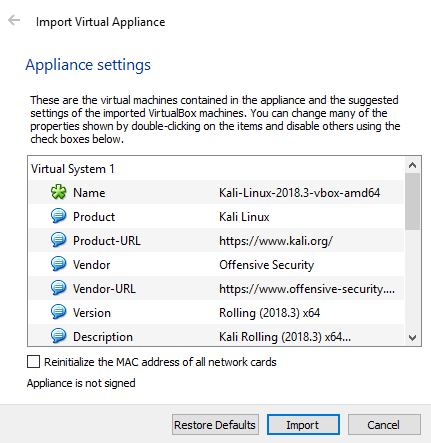
After downloading, you will get a file with the .ova extension. Now, to install the Kali Linux, you need to just double click on the file and click on the import button.
After installation, the Kali Linux is ready to use and will look like as follows:
Clicking the links below will directly take you to their Hacking Coures.
1.Penetration Testing.
2. Complete the Hacking course.
Link to this Course ;)
3. Ethical Hacking with Kali Linux.
4.Full Hacking Course.
5.The complete ethical hacking course.
6.Beginners course for hacking.
Playlist for this course
7. Learn Wifi Hacking (HINDI).
Click here for the full playlist.:)
8. UDEMY FREE COURSE.
Click here for the full playlist. :)
9.
Click here for the full playlist. :)
10.
11.Hacking + Cyber Security(BONUS) :)
Click here for the full playlist. :)
~TOP 10 BEST HACKING WEBSITE.
Clicking the links below will directly take you to their Hacking Coures.
1.CYBRARY (RECOMMENDED)
2.Security Tube
3.edX
4.SANS Cyber Aces
5.javatpoint (RECOMMENDED)
6.tutorialspoint (RECOMMENDED)
7.Hacking Tutorial
8.Hack in the box
9.Hack this site
10.Hack a day
11 .Udemy(paid)
~SOME GREAT HACKING BOOKS ON AMAZON.(FREE PDF).
Amazon link has been given and also the level of books plz buy according to your Level
1. The Hackers Playbook by Peter Kim.
Level: Beginner Friendly!
Buy on amazon
2.The Hackers Playbook 3
Buy on amazonLevel: Beginner Friendly!
Buy on amazon
2.The Hackers Playbook 3
by Peter Kim
Level: Beginner Friendly!
3.Rtfm: Red Team Field Manual
by Ben Clark
Level: All levels
4.Hacking: The Art of Exploitation, 2nd Edition
by Jon Erickson
Level: Intermediate
Buy on amazon
The Web Application Hacker’s Handbook: Finding and Exploiting Security Flaws
by Dafydd Stuttard & Marcus Pinto
Level: Beginner-Intermediate
Buy on amazon
Penetration Testing: A Hands-On Introduction to Hacking
by Georgia Weidman
Buy on amazon
Kali Linux Revealed: Mastering the Penetration Testing Distribution
by Raphael Hertzog & Jim O’ Gorman
Level: Beginner-Advanced
Ghost in the Wires: My Adventures as the World’s Most Wanted Hacker
by The Legend Himself, Kevin Mitnick
Level: All levels
Advanced Penetration Testing: Hacking the World’s Most Secure Networks
by Will Allsopp
Level: Advanced
Honorable Mention: Hacking mit Metasploit
by Michael Messner
Level: Beginner-Advanced
Language: German
Buy on amazon
~FAMOUS ETHICAL HACKERS
1.Jonathan James
Jonathan James was an American hacker. He is the first Juvenile who send to prison for cybercrime in the United States. He committed suicide on 18 May 2008, of a self-inflicted gunshot wound.
In 1999, at the age of 16, he gained access to several computers by breaking the password of a NASA server and stole the source code of International Space Station, including control of the temperature and humidity within the living space.
2.Kevin Mitnick
He is a computer security consultant, author, and hacker. He infiltrates his client's companies to expose their security strengths, weaknesses, and potential loopholes. In the history of the united state, he was formerly the most wanted computer criminal.
From the 1970s up until his last arrest in 1995, he skillfully bypassed corporate security safeguards and found his way into some of the most well-guarded systems like Sun Microsystems, Nokia, Motorola, Netcom, Digital Equipment Corporation.
3.Mark Abene
Mark Abene is an American Infosec expert and Entrepreneur. He is known around the world by his pseudonym Phiber Optik. Once, he was a member of the hacker groups Legion of Doom and Master of Deception. He was a high profile hacker in the 1980s and early 1990s.
He openly debated and defended the positive merits of ethical hacking as a beneficial tool for the industry. He is also an expert in penetration studies, security policy review and generation, on-site security assessments, systems administration, and network management, among many others.
4.Robert Morris
Robert Morris was the creator of the Morris Worm. He was the first computer worm to be unleashed on the Internet. The Morris Worm had the capability to slow down computers and make them no longer usable. Due to this, he was sentenced to three years probation, 400 hours of community service and also had to pay a penalty amount of $10,500.
5.Gary McKinnon
Gary McKinnon is a Scottish systems administrator and Hacker. In 2002, he was accused of the "biggest military computer hack of all time". He has successfully hacked the network of Navy, Army, Air Force, NASA system of the United States Government.
In his statement to the media, he has often mentioned that his motivation was only to find evidence of UFOs and the suppression of "free energy" that could potentially be useful to the public.
6.Linus Torvalds
Linus Torvalds is a Finnish-American software engineer and one of the best hackers of all time. He is the developer of the very popular Unix-based operating system called Linux. Linux operating system is open source, and thousands of developers have contributed to its kernel. However, he remains the ultimate authority on what new code is incorporated into the standard Linux kernel.
Torvalds just aspire to be simple and have fun by making the world's best operating system. Linus Torvalds has received honorary doctorates from the University of Helsinki and Stockholm University.
7.Kevin Poulsen
Kevin Poulsen is an American former Black-hat hacker. He is also known as Dark Dante. He took over all the telephone lines of radio station KIIS-FM of Los Angeles, guaranteeing that he would be the 102nd caller and win the prize of a Porsche 944 S2.
Poulsen also drew the ire of FBI, when he hacked into federal computers for wiretap information. As a result of this, he was sentenced for five years. He has reinvented himself as a journalist.
~INDIAN HACKERS.
1.Rishiraj Sharma
2..Ankit Fadia
3.Vivek Ramachandran
4.Sai Satish
5.Sunny Vaghela
6.Rahul Tyagi
7.Pranav Mistry
8.Trishneet Arora (MY INSPIRATION)
9.Falgun Rathod
10.Rajesh Babu
~MY MOTIVATION
Among all the above hackers my motivation is TRISNEET ARORA, I find him to be a very talented hacker. Being a school dropout he with his extraordinary talent learned hacking and opened a company called TAC security which is worth crores, on the other hand, he was class 8 fail guy so is truly inspirational. So, that was my inspiration comment down yous inspiration.
~CONCLUSION.
"However a system is secured, it cannot be protected from a HACKER"
Though hacking has its pros and cons we should use our hacking power wisely. It must be kept in mind that you can even be sentenced to jail if found doing illegal hacking. But ETHICAL HACKING" is legal yes you can practice it at your home.
So, start your journey today and shine in the future and i will be always be there to support you through my skills but don't forget to SUBSCRIBE to my blog.
With best wishes HAPPY LEARNING !!
Me, Ayan De(Kolakta,India)
Signing out...























good
ReplyDeleteFULLZ AVAILABLE WITH HIGH CREDIT SCORES 700+
Delete(Spammed From Credit Bureau of USA)
=>Contact 24/7<=
Telegram> @leadsupplier
ICQ> 752822040
Email> exploit.tools4u@gmail.com
FRESHLY SPAMMED
VALID INFO WITH VALID DL EXPIRIES
*All info included*
NAME+SSN+DOB+DL+DL-STATE+ADDRESS
Employee & Bank details included
CC & CVV'S ONLY USA $8 FOR EACH
$1 for SSN+DOB
$2 for SSN+DOB+DL
$5 for High credit fullz 700+
(bulk order negotiable)
*Payment in all crypto currencies will be accepted
->You can buy few for testing
->Invalid or wrong info will be replaced
->Serious buyers needed for long term
->Very fast delivery
PLEASE DON'T ASK ANYTHING FOR FREE
TOOLS & TUTORIALS AVAILABLE FOR SPAMMING & HACKING
(Carding, spamming, hacking, scam page, Cash outs, dumps cash outs)
SQL Injector = 250$
Premium Accounts (Netflix, coinbase, FedEx, Pornhub, etc) =25$
Paypal Logins = 150$ (10 Logins)
Bitcoin Cracker = 500$
SMTP Linux Root = 300$
DUMPS with pins track 1 and 2 = 85$
Socks, rdp's, vpn = 25$
Php mailer = 25$
Server I.P's = 100$ (1k ip's)
HQ Emails with passwords = 100$ (1k emails+pass)
*If you need a valid vendor it's very prime chance, you'll never be disappointed*
Telegram> @leadsupplier
ICQ> 752822040
Email> exploit.tools4u@gmail.com
Wow nice 👍👍👍👍 content loved it..
ReplyDeleteNice keep it up
ReplyDeleteNice
ReplyDeleteamazing
ReplyDeleteclick me
thank you guys
ReplyDelete///SPONSORED ADVERT///
ReplyDeleteTRACK ANY PHONE LOCATION
HACK ANY FACEBOOK ACCOUNT
HACK INSTAGRAM ACCOUNT
SPY ON YOUR CHEATING PARTNER
READ OTHERS WHATSAPP MESSAGES
TRACK BITCOIN WALLET OWNER
GET 50K INSTAGRAM FOLLOWERS FOR 50 USD (REAL PEOPLE)
GET 30K INSTAGRAM FOLLOWERS FOR 30 USD (REAL PEOPLE)
READ ANY PHONE SMS
SS7 SIGTRAN AVAILABLE
2 FACTOR AUTHENTICATION BYPASS (NEW)
GET USA/CANADA/EUROPE DRIVING LICENSE
i also teach how to channel unconfirmed BTC to your own wallet(LIMITED)
CONTAC: teamhackworld@gmail.com
Mobile : +1 (512) 956 5704
WEBSITE: http://pladollmo.com/28Jv
ReplyDeleteIt was great experience after reading this. thanks for sharing such good stuff with us.
Ethical Hacking Course in Delhi
thanks Atul
DeleteHi Clients!
ReplyDeleteWe have fresh and valid usa ssn leads
100% good and valid leads
*If you have any trust issue before any deal you may get few to test
*Every leads are well checked and available 24 hours
****Contact Me****
*ICQ :748957107
*Gmail :taimoorh944@gmail.com
Cost for Premuim lead $5 for each
Cost for normal lead $2 for each
Price can be negotiable if order in bulk
*please contact soon!
*I hope a long term deal
*Thank You
How To Become an Ethical Hacker | Beginners Guide
ReplyDeleteHello all
ReplyDeleteam looking few years that some guys comes into the market
they called themselves hacker, carder or spammer they rip the
peoples with different ways and it’s a badly impact to real hacker
now situation is that peoples doesn’t believe that real hackers and carder scammer exists.
Anyone want to make deal with me any type am available but first
I‘ll show the proof that am real then make a deal like
Available Services
..Wire Bank Transfer all over the world
..Western Union Transfer all over the world
..Unlock Iphone / Andriod
..Credit Cards (USA, UK, AUS, CAN, NZ)
..School Grade upgrade / remove Records
..Spamming Tool
..keyloggers / rats
..Social Media recovery
.. Teaching Hacking / spamming / carding (1/2 hours course)
discount for re-seller
Contact: 24/7
fixitrogers@gmail.com
ACTIVE & FRESH CC FULLZ WITH BALANCE
ReplyDeletePrice $5 per each CC
US FRESH, TESTED & VERIFIED SSN LEADS
$1 PER EACH
$5 FOR PREMIUM DATA
CC DETAILS
=>CARD TYPE
=>FIRST NAME & LAST NAME
=>CC NUMBER
=>EXPIRY DATE
=>CVV
=>FULL ADDRESS (ZIP CODE, CITY/TOWN, STATE)
=>PHONE NUMBER,DOB,SSN
=>MOTHER'S MAIDEN NAME
=>VERIFIED BY VISA
=>CVV2
SSN LEADS INFO
First Name | Last Name | SSN | Dob | Address | State | City | Zip | Phone Number | Account Number | Bank NAME | DL Number | Home Owner | IP Address |MMN | Income
Contact Us
-->Whatsapp > +923172721122
-->Email > leads.sellers1212@gmail.com
-->Telegram > @leadsupplier
-->ICQ > 752822040
*You can buy for your specific states too
*Payment in advance
*Hope for the long term deal
*Time wasters or cheap questioners please stay away
*If you buy leads in bulk, I'll definitely negotiate
*You can ask me for sample of Lead for demo
US DUMP TRACK 1 & 2 WITH PIN CODES ALSO AVAILABLE
Hey Guys !
ReplyDeleteUSA Fresh & Verified SSN Leads with DL Number AVAILABLE with 99.9% connectivity
All Leads have genuine & valid information
**HEADERS IN LEADS**
First Name | Last Name | SSN | Dob | DL Number | Address | City | State | Zip | Phone Number | Account Number | Bank Name | Employee Details | IP Address
*Price for SSN lead $2
*You can ask for sample before any deal
*If anyone buy in bulk, we can negotiate
*Sampling is just for serious buyers
==>ACTIVE, FRESH CC & CVV FULLZ AVAILABLE<==
->$5 PER EACH
->Hope for the long term deal
->Interested buyers will be welcome
**Contact 24/7**
Whatsapp > +923172721122
Email > leads.sellers1212@gmail.com
Telegram > @leadsupplier
ICQ > 752822040
Bonjour les gars, si vous avez besoin d'embaucher un vrai hacker pour surveiller / pirater le téléphone de votre partenaire à distance, échanger et doubler votre argent en quelques jours / semaines, ou pirater une base de données, le tout avec confidentialité garantie, contactez easybinarysolutions@gmail.com, ou whatsapp: +1 3478577580, ils sont efficaces et confidentiels.
ReplyDeleteI really enjoy the blog article.Much thanks again.
ReplyDeleteios training
Iot online training
Iot training
Java online training
Java training
Machine learning online training
Machine learning training
Magento online training
Your website is terribly informative and your articles are wonderful.
ReplyDeleteOnline Hacking Institute in Jaipur
Ethical Hacking Course in Noida
ReplyDeleteNice Post...
ReplyDeleteI'm having very interesting information regarding Hacker for Hire
Nice Post....
ReplyDeleteI'm having very interesting information regarding Hire A Hacker, Ethical Hacker for Hire and Hire Professional Hackers!
It was great experience after reading this.
ReplyDeleteEthical Hacking Training in Gurgaon
Ethical Hacking Course in Gurgaon
Nice Post...
ReplyDeleteI'm having very interesting information regarding Hire A Hacker!
Selling USA FRESH SPAMMED SSN Leads/Fullz, along with Driving License/ID Number with EXCELLENT connectivity.
ReplyDelete**PRICE**
>>2$ FOR EACH LEAD/FULLZ/PROFILE
>>5$ FOR EACH PREMIUM LEAD/FULLZ/PROFILE
**DETAILS IN EACH LEAD/FULLZ**
->FULL NAME
->SSN
->DATE OF BIRTH
->DRIVING LICENSE NUMBER WITH EXPIRY DATE
->ADDRESS WITH ZIP
->PHONE NUMBER, EMAIL, I.P ADDRESS
->EMPLOYEE DETAILS
->REALTIONSHIP DETAILS
->MORTGAGE INFO
->BANK ACCOUNT DETAILS
>All Leads are Tested & Verified.
>Invalid info found, will be replaced.
>Serious buyers will be welcome & I will give discounts for bulk orders.
>Fresh spammed data of USA Credit Bureau
>Good credit Scores, 700 minimum scores
>Bulk order will be preferable
>Minimum order 20 leads/fullz
>Hope for the long term business
>You can asked for samples, specific states & zips (if needed)
>Payment mode BTC, PAYPAL & PERFECT MONEY
Email > leads.sellers1212@gmail.com
Telegram > @leadsupplier
ICQ > 752822040
''OTHER GADGETS PROVIDING''
>Dead Fullz
>Carding Tutorials
>Hacking Tutorials
>SMTP Linux Root
>DUMPS with pins track 1 and 2
>Sock Tools
>Server I.P's
>USA emails with passwords (bulk order preferable)
**Contact 24/7**
Email > leads.sellers1212@gmail.com
Telegram > @leadsupplier
ICQ > 752822040
Excellent information against Unethical Cyber crime! Cyber criminals do not mind targeting corporations and businesses as long as they can use them as a way to escape from the law. Because of this the only way to curb cyber crimes not working for the government is to put in place measures that will hinder the resources of these cyber criminals. The most common measures include creating more stringent laws regarding copyright and intellectual property theft. Various government agencies watch activities of unethical Cyber crimes. They can find Hacker for Hire for ethical work. A ethical hacker can resolve the critical issues.
ReplyDeleteNice Post!!
ReplyDeletePlease look here at Hire A Professional Hacker
This is one of the useful content. The truth is, they only require a little guidance and practice, but they can go a long way. Hackers usually start out using trial and error to determine what kind of hacking they're doing. Once they've determined the right technique, they'll continue to refine and improve their technique until they're proficient enough to launch a successful hack. So if you think you may need help with a technical problem, there are a few things you can do to find a good hack lancer.
ReplyDeletehire a hacker
You can rent a hacker with deliver the work and task assignment within 24 hours to 5 days. If you are not satisfied with our services, you will be definitely refunded without any questions!
ReplyDelete1. Server security related services
2. Crypto-currency related services
3. Lost/stolen Bitcoin recovery services
4. Credit score related services
5. College/university grade change services
6. Get rid from cyber stalking
7. Get rid from cyber bullying
8. Get rid from extortion
9. Trace ip address
Write for Us
Nice Post!!
ReplyDeletePlease look here at Professional Hackers for Hire
Ethical Hackers for Hire
Hire A Professional Hacker
Legit Hackers For Hire
Hire A Hacker
Hacker for Hire
Nice Blog information! Do you know? Spy and Monitor have specialist dark web team. We have already served in the Dark Web a long time ago. After many requests we now want to explicitly offer our hacking services to all. We want to stay alive. Hope you all help us to live and offer you our services.
ReplyDeleteYou can find and hire a hacker online!
Excellent blog content. I would like to thanks for sharing blog information. If you are one of those people who are trying to find out how to hire a hacker or a professional Private Investigator, then you must be wondering where to start. You need not worry; all you need is the right information. If you want to find the right Private Investigator, then you have come to the right place. Here, you are going to learn some of the ways in which you can find a legitimate and reputed Private Investigator easily. So, let us begin.
ReplyDeleteThe very first thing that you should do is not to believe in anything that you read on the Internet or on TV. You have to take your own initiative in this matter. Do not rely on what others are saying. Also, do not fall for the most common misconception that you can catch a cheater by having a camera handy. This is absolutely false!
When it comes to this subject, this site https://onionlinks.com/ is a good guide.
ReplyDeleteThis is outstanding blog information you have post. I would like to thanks for sharing the information. So are you searching for a private investigator? For one thing, they are much more likely to find something on you. If you think about it, a private investigator has many resources. He or she might have access to a spy program, a computer that was broken into, etc. A hacker doesn't have any of those tools.
ReplyDeleteWhere to find a private investigator?
Do not worry about it! You can hire a hacker by professional team of hackers online. Professional hackers will also get you in trouble sometimes. Hiring someone to get a hold of your phone (or systems) means that they will be able to see what you're doing on it. This includes texting and emailing (or both). Hackers will be able to see all of this as well and may have already done some of it. Always find ethical hackers. Thanks again for sharing information.
Hi Guy's
ReplyDeleteFresh & valid spammed USA SSN+Dob Leads with DL available in bulk.
>>1$ each SSN+DOB
>>2$ each with SSN+DOB+DL
>>5$ each for premium (also included relative info)
Prices are negotiable in bulk order
Serious buyer contact me no time wasters please
Bulk order will be preferable
CONTACT
Telegram > @leadsupplier
ICQ > 752822040
Email > leads.sellers1212@gmail.com
OTHER STUFF YOU CAN GET
SSN+DOB Fullz
CC's with CVV's (vbv & non-vbv)
USA Photo ID'S (Front & back)
All type of tutorials available
(Carding, spamming, hacking, scam page, Cash outs, dumps cash outs)
SMTP Linux Root
DUMPS with pins track 1 and 2
Socks, rdp's, vpn's
Server I.P's
HQ Emails with passwords
Looking for long term business
For trust full vendor, feel free to contact
CONTACT
Telegram > @leadsupplier
ICQ > 752822040
Email > leads.sellers1212@gmail.com
Your blog is completely unique. This isn't regular which usually you discover ambition reports relating to the essay writing services reviews offerings and additionally systems. Almost all people only just discover it straightforward to support a lot of creators and not just still produce that is why hire a hacker service to guide you.
ReplyDeleteYou as beginner and you need to hire a hacker, it has to been from a company that are highly recommended with different type of job render to client. I believe they are show you the ethic of hacking with technical way
ReplyDeleteThey are different way you can hire a cheap hacker, which can assist you to actualize your dream. This blog has all the information that is available on internet such as:
ReplyDeleteUniversity Grades changing
+Erase Criminal Records hack
+ Hack Driver License
+Facebook hack, Twitter hack, Instagram hack, Gmail, Yahoo hack
+Already hacked PayPal, MasterCard, Credit Card untraceable balance
+Email interception hack
+Hack computer remotely
+Whats-app hack
+Email accounts hack
+hack into any database
+Bank accounts hack
+Hack WORD-PRESS Blogs
+Untraceable IP and all degree of hacking.
database hacking Des-: Tentronix is India’s best CCTV Company & Security Products and Solutions Manufacturer. Our main products are CCTV Cameras, Access &;Control, Automation; Security Equipments. Call us now for home & office CCTV Camera & Security Camera installation.
ReplyDeleteThank you for sharing such a nice blog. It's really impressive. I appreciate your intelligence and knowledge. This blog is really beneficial for many of us. Here is something related to cyber security online certification courses
ReplyDeleteWhat a great information If you ever need hacking services, we are just a step away Hire a hacker on the Dark Web Now
ReplyDeleteHire a white hat hacker now For
ReplyDeleteSchool grade hack
facebook hack
email hack
whatsapp hack
Phone hack
School / University grades hack
Transcripts
GPA hack
Boost credit score
Database hack
Hire only the Best
Hack your husbands phone with ease without him knowing
ReplyDeleteTrusted hackers online
Hack husbands whatsapp messages remotely
Are you looking for certified ethical hackers for hire? We provides website hacking, computer hacking, email hacking services at best price. For more details visit us now.Best Computer Hacking Services Hire Online
ReplyDeleteHire A Hacker | Ethical Hackers For Hire | Anonymous Hack
ReplyDeleteWe provide the best professional and certified ethical hackers like social media, cell phone, email, website, etc. Our hackers are well experienced and most trusted.
For More Info:- Hire a hacker online
This comment has been removed by the author.
ReplyDeleteIt was a great blog Thanks for sharing. But if anyone looking for Ethical Hacking Course within affordable price. We have the solution.
ReplyDeleteThank you for sharing this information with us. Learn Ethical Hacking Course and you will get more Information about Ethical hacking. In this Ethical Hacking Ethical hacking Training and Certification Course in Delhi, you will learn how to hack the system passwords, Mobile hacking, web Hacking, SQL Injection, etc.
ReplyDeleteEthical Hacking Course
I have found that this site is very informative, interesting and very well written. keep up the nice high quality writing
ReplyDeleteAdvanced Penetration Testing Certification Course
Cyber Crime Awareness Society (CCAS) is a leading organization in the fields of Cyber Security. The advancement in the technology has made a great change in the internet world. But with these advancements arises the need to secure our data too. Therefore, we aim to digitally shield the cyber space by providing you the beneficial knowledge. We are hovering to influence our proficiency in ethical hacking and creating a global footprint in the fields of cyber security and cyber crime awareness. Our organization foster certified trainings in ethical hacking and various other sectors to meet the specific needs of our students.
ReplyDeleteVisit here - Cyber Security Course In Jaipurr
Nice post kep sharing such informative blog. Apply for best training in Ethical Hacking.
ReplyDeleteFULLZ AVAILABLE WITH HIGH CREDIT SCORES 700+
ReplyDelete(Spammed From Credit Bureau of USA)
=>Contact 24/7<=
Telegram> @leadsupplier
ICQ> 752822040
Email> exploit.tools4u@gmail.com
FRESHLY SPAMMED
VALID INFO WITH VALID DL EXPIRIES
*All info included*
NAME+SSN+DOB+DL+DL-STATE+ADDRESS
Employee & Bank details included
CC & CVV'S ONLY USA $8 FOR EACH
$1 for SSN+DOB
$2 for SSN+DOB+DL
$5 for High credit fullz 700+
(bulk order negotiable)
*Payment in all crypto currencies will be accepted
->You can buy few for testing
->Invalid or wrong info will be replaced
->Serious buyers needed for long term
->Very fast delivery
PLEASE DON'T ASK ANYTHING FOR FREE
TOOLS & TUTORIALS AVAILABLE FOR SPAMMING & HACKING
(Carding, spamming, hacking, scam page, Cash outs, dumps cash outs)
SQL Injector = 250$
Premium Accounts (Netflix, coinbase, FedEx, Pornhub, etc) =25$
Paypal Logins = 150$ (10 Logins)
Bitcoin Cracker = 500$
SMTP Linux Root = 300$
DUMPS with pins track 1 and 2 = 85$
Socks, rdp's, vpn = 25$
Php mailer = 25$
Server I.P's = 100$ (1k ip's)
HQ Emails with passwords = 100$ (1k emails+pass)
*If you need a valid vendor it's very prime chance, you'll never be disappointed*
Telegram> @leadsupplier
ICQ> 752822040
Email> exploit.tools4u@gmail.com
Ethical hacking courses for fledglings seeking to pro the ethical hacking field.
ReplyDeleteEthical Hacking Training Course in Noida
ReplyDeleteIt's really nice and meaningful. it's really cool blog, Thank you.
ReplyDeletekali linux training courses in malaysia
Beware of scammers i have been scammed 3 times because i was trying to know if my husband was cheating until i met this hacker named; (wizardcyprushacker@gmail.com) who helped me hack into my spouse phone for real this great hacker hacked into my spouse whats-app messages,Facebook messages.text messages,call logs,deleted text messages,bitcoin recovery and bank transfer hack,clear criminals records,and many more i was impressed with his job and he brought me results under 24 hours believe me he is real and his services are cheap and affordable. whatsapp +1 (424) 209-7204
ReplyDeleteDo you suspect your spouse of cheating, are you being overly paranoid or seeing signs of infidelity...Then he sure is cheating: I was in that exact same position when I was referred to (wizardcyprushacker@gmail.com) through my best friend Anna, who helped me hack into my boyfriend's phone, it was like a miracle when he helped me clone my boyfriend's phone and I got first-hand information from his phone. Now I get all his incoming and outgoing text messages, emails, call logs, web browsing history, photos and videos, instant messengers(facebook, whatsapp, bbm, Instagram, etc) , GPS locations, phone tap to get live transmissions on all phone conversations. If you need help contact him on email, (wizardcyprushacker@gmail.com) or Whatsapps:+1 (424) 209-7204 I guarantee you for reliable service. Tell him I referred you.
ReplyDeleteCan’t believe darkhatthacker@gmail.com hacked 3 yahoo accounts in the space of just 40min and got me results of all without any trace or notifications, darkhatthacker@gmail.com your indeed wonderful Thank you.
ReplyDeleteHey! I have read your blog, it is very well-written content that you have shared here. I have learned many things related to .
ReplyDeleteethical hacking training
Thank you for sharing it
Get hidden secret messages from your partners phone with the help of darkhatthacker@gmail.com and thank me later, this is the hacker that works for me also and I got a lot of testimonies about darkhatthacker@gmail.com on his great services.
ReplyDeleteEthical Hacking Course in Noida
ReplyDeleteWe are Providing the Best Ethical Hacking Course training. Visit :-
ReplyDeleteEthical Hacking Course in Kolkata
Ethical Hacking Course in Bangalore
It is really very helpful for us and I have gathered some important information from this blog.
ReplyDeleteAdvanced penetration testing certification course
Thanks for writing such a good article, I stumbled onto your blog and read a few post. I like your style of writing...
ReplyDeleteHire Hacker
Ethical Hacking course in Gurgaon
ReplyDeleteHey! I have read your blog, it is very well-written content that you have shared here. I have learned many things related to .
ReplyDeleteethical hacking course in bangalore
Thank you for sharing it
Contact (wizardcyprushacker@gmail.com) whatsapp +1 (424) 209-7204 for any hacking job he is the best among all.
ReplyDeleteFew days after my boyfriend proposed to me I caught him cheating on me with the help of an expert hacker after I hired this hacker to get me full informations of my boyfriend phone and behold after going through his phone I saw a lot that broke my heart, but I thank God and I thank spyexpert0@gmail.com for this phone hack that made me know who the man I was about getting married to is.
ReplyDeleteNice post thanks for sharing a very informative article about Complete Hacking Course Beginners to advanced
ReplyDelete